Since 1995
Managed Cybersecurity for Financial Services
Preventing Breaches, Fines, & Cyber Insurance Claim Declinations

Enterprise Cybersecurity for the Field
Independent Agents, Advisors, Agencies, Branches, and Home Offices
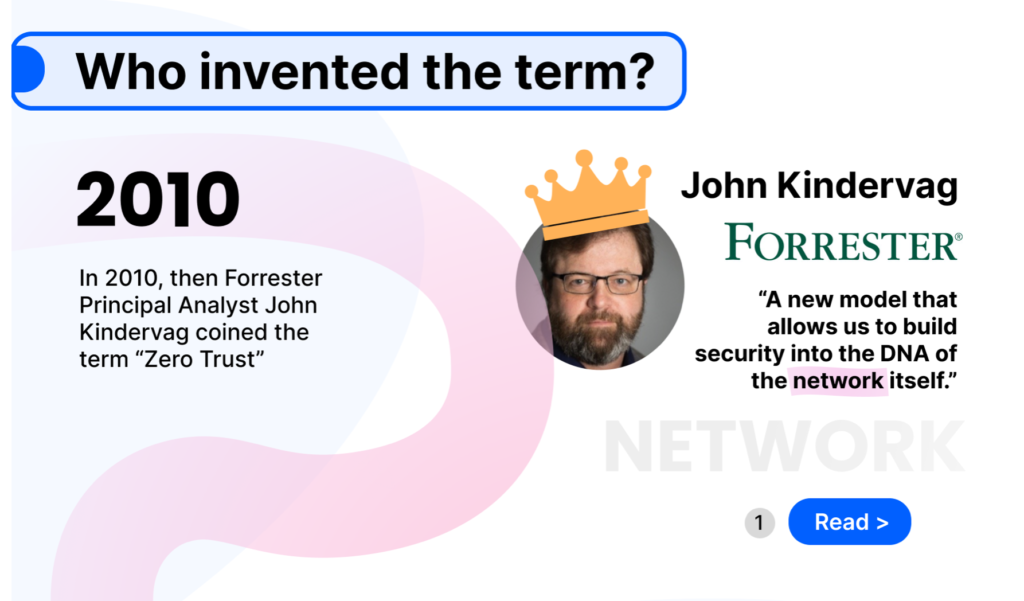
Zero-Trust Managed Cybersecurity Services
For Your Firm Security & Compliance
Endpoint
Security
Automating and managing the enforcement of cyber settings and advanced endpoint protection
User
Security
Verifying that only authorized users can access data, endpoints, software, and networks
Network Security
Enforcing secure and encrypted communication inside and outside corporate networks
Cloud App Security
Hardening software and validating the compliance of users, and networks at the time of login
Zero-Trust Managed Cybersecurity Services
End-to-End Cybersecurity Protection & Compliance
A solution that augments and adapts to teams, skill sets and systems already in place
Co-Managed Cyber Services
How FCI partners with Enterprises, internal IT teams, and MSPs
Testimonials
“We strongly recommend FCI to any firm with a desire to get cybersecurity protection and compliance.”
Nash Subotic, Founder & CEO
Westpac Wealth Partners

WestPac is an Agency of The Guardian Life Insurance Company of America
Are you ready for a breach?
There are specific steps, language, evidence and protocols to follow to ensure you are protected and ready to handle cyber situations.
What to do
Do you know the exact steps to take for incidents and breaches to ensure compliance at both the Home Office and Branch or Agency levels?
What to preserve
Do all parties know how to preserve evidence if an incident or breach happens?
What to say
Do you know how to speak to Cyber Insurers and the FBI when they question you about a breach?
MANAGED CYBERSECURITY SERVICES
The 1-Question
Compliance Check
To meet cybersecurity regulations and stay safe
How cybersecurity impacts company valuation in M&A transactions
Are you buying firms or selling yours?
Get an FCI Security Assessment performed to reduce liabilities



"FCI CEO Brian Edelman is one of the few real cybersecurity experts who understand compliance...
A true thought leader"
Joel Bruckenstein

Are you prepared for a Zero Trust audit?
At any time, regulators, authorities, and cyber insurers can knock at your door and ask for evidence of compliance. With a short complimentary call with Managed Security Service Provider FCI, we will let you know.
Request a quick cybersecurity assessment